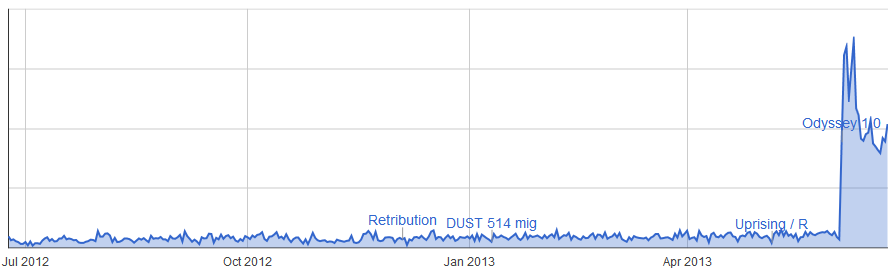
It's been several weeks since the launch of Odyssey and the introduction of new mechanics in exploration sites by Team Prototyping Rocks. Since the launch we've been tracking usage statistics for our features and this devblog is going to take a look at some of the more interesting things we've seen from the high-level statistics. All of this has been made possible by a push towards gathering a lot more metrics from the game. Team Data, our dedicated metrics guys have given us some really powerful tools to crunch logs and generate the information below.
Impact on Exploration Sites
There have been two major changes to exploration that impact on the graphs I'm going to show. It's much less painful to scan sites down which means more people should spend time doing it and the mechanics in the newly named Data and Relic sites are different than they were previously therefore more people might want to spend time finding them.
First we'll look at the top three (by completions) Data and Relic sites:
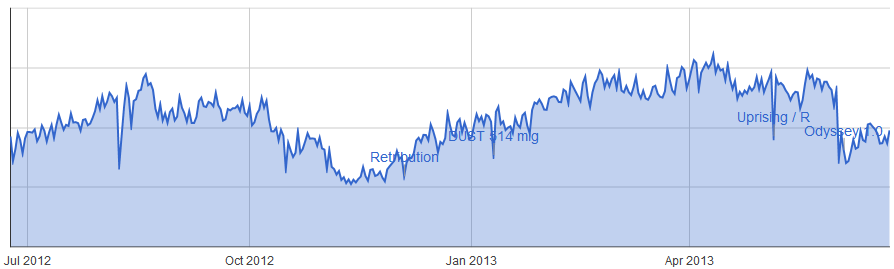
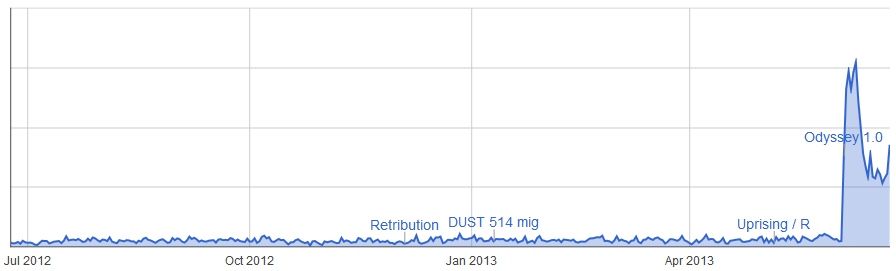
Ruined Guristas Monument Site (null-sec)
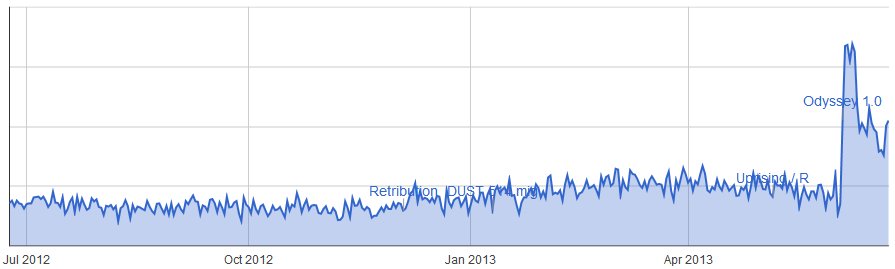
Central Guristas Sparking Transmitter (null-sec)
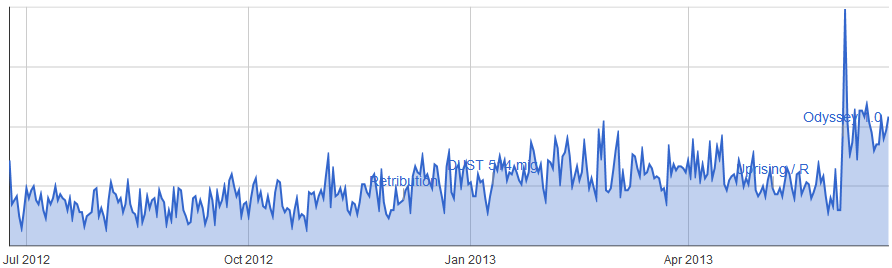
Local Guristas Virus Test Site (high-sec)
It's pretty clear from these three graphs that usage and completion of these sites has increased immensely since the launch of Odyssey. Some of them very significantly, for example the Sparking Transmitter site has seen a near ten-fold increase in usage even if we ignore the initial release spike. Significantly the first two sites are only found in 0.0 space. In high-sec there is again a significant increase in traffic but this time only twice as many sites are being completed.
In the interests of comparison we should take a look at the Combat Sites being scanned down. Here is the top null-sec site by completions and the top high-sec site by completions:
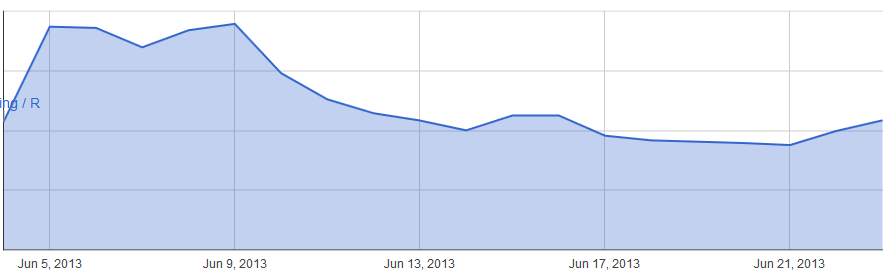
Sansha Hideout (high-sec/low-sec)
High-sec at least seems to be on a similar trend, albeit with a much smaller jump in usage but what on earth happened to null-sec Combat Sites? We'd need to gather some more information to find out exactly but clearly people are much less interested in them now. I'd be inclined to hypothesize that people are typically out exploring null-sec in cloaky frigates as rats have been removed from the Data and Relic sites and they are reasonably effective for avoiding other players, so the Combat Sites in null-sec are out of most ship capabilities without having to multi-box or reship.
Whatever the reason for the dip in use of Combat Sites in null-sec it's clear that the Data and Relic sites are seeing much more traffic across the board and seem to be trending towards stabilizing at a much higher level of use than before. When compared to Combat Sites that have followed a similar trend they are still more popular suggesting that there is more at play than just an increased ability to find these sites.
Hacking
The trend for total Hacking attempts since launch looks like this:
Total Hacking Attempts Per Day
Here we can quite clearly see the initial interest and gold rush as people attempted to get rich before the market value of the loot dropped thanks to the increased supply. After which we can clearly see the next two weekends highlighted by the increased activity. I expect the trend to level out somewhere in the region of 100,000 attempts per day. It might even trend higher as the market recovers from the initial onslaught and we've recently fixed a bug that meant sites were not respawning as they should. This is a figure we can watch as a good 'large-scale' judge of changes we make to Hacking.
In the above graph you can see that the global win/loss ratio quickly stabilized. Currently around 65% of Hacking attempts are successful. As a metric this is interesting as a high level view of how hard hacking is for the player base. However we have way more data and are working on automating finer grained metrics to let us see how successful people were depending on their ship, skill, rigs, etc. across various difficulty tiers.
Scattering
As you would expect from a mechanic closely related to the Hacking the scattering usage graphs follow a very similar pattern so we'll skip those for now. However the ratio of the cans collected to lost is very interesting when we take a look at the types of container:
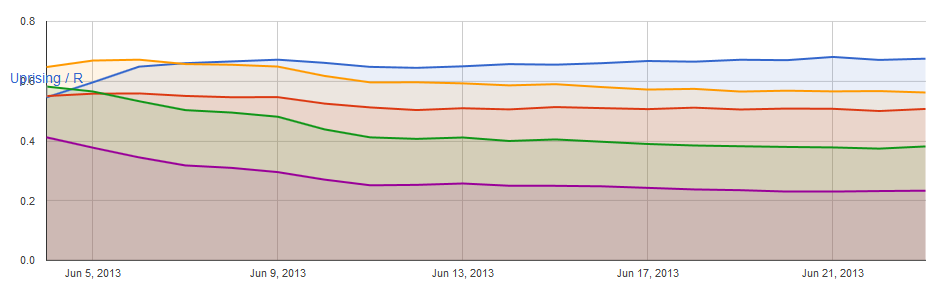
Ratio of Cans Collected by Type
(Blue – Parts, Orange – Materials, Red – Data, Green – Equipment, Purple – Scraps)
We can see within a week of release that the player population had generally worked out what was and wasn't worthwhile to take. This graph also shows that quite a large number of cans are going uncollected, losing whatever value they happened to contain. We'll have to do some more digging to see how much value is represented there.
Summary
This has just been a quick poke through the high-level statistics we have for our exploration site changes. Part of our work towards Odyssey 1.1 involves getting more fine grained statistics into our automated tools so we can track changes we make to Hacking and Scattering in the future. We'll doubtless be back with more information in the future and I'm sure other teams will be along shortly with more pretty, pretty graphs.
New to EVE? Start your 14-day free trial today.
Returning pilot? Visit Account Management for the latest offers and promotions.